Authentication with Google Secure LDAP Service
Table of Contents
Version: 19th May 2025
1. Introduction
This document describes primary user authentication to Google LDAP Server for Windows Workstations and Windows Servers using the Comtarsia Logon Client.
A prerequisite is a Google Frontline/Business/Education/Enterprise account where LDAP services are available.
The Google LDAP server requires the client to use client certificates. This is not very common with LDAP servers and therefore, the Comtarsia Logon Client itself does support this via an external free service, Stunnel. This guide describes the method suggested by Google, using the free tool stunnel.
Further information on how to set up clients to use the Google Secure LDAP service can be found here: https://support.google.com/a/answer/9089736
2. Setup LDAP Client in Google LDAP Server
First, an LDAP client must be added in your Google Workspace Admin console.
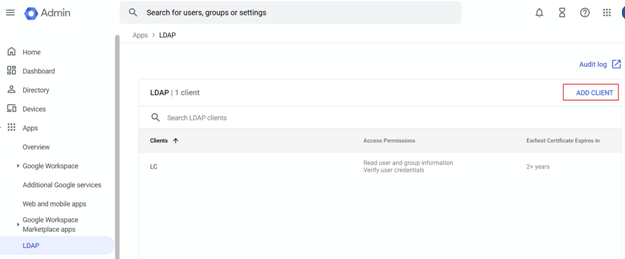
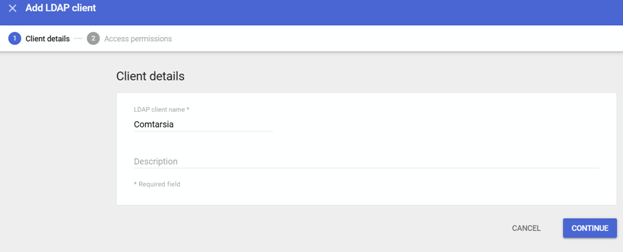
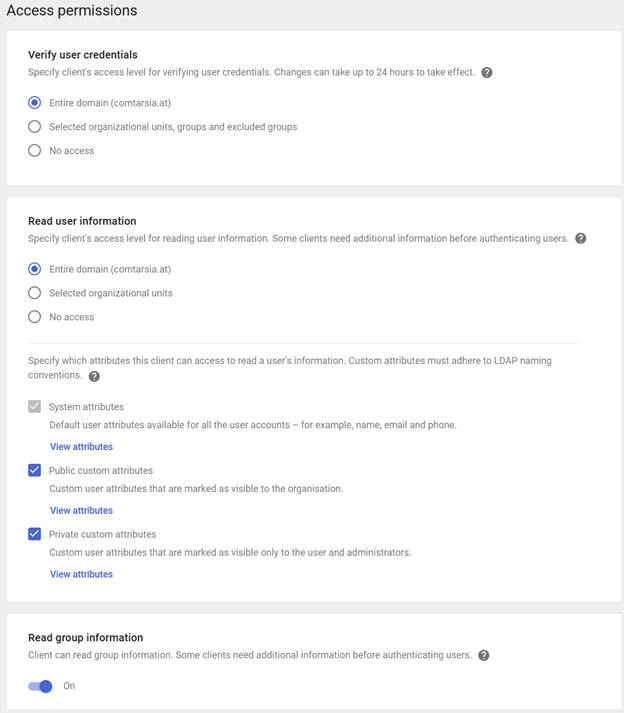
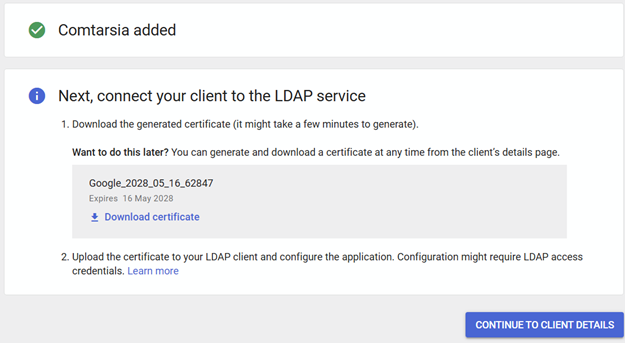
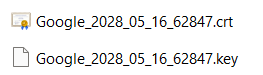
Download the certificates for this LDAP Client connection and make these files available to the Windows client. The use is described in the following chapter.
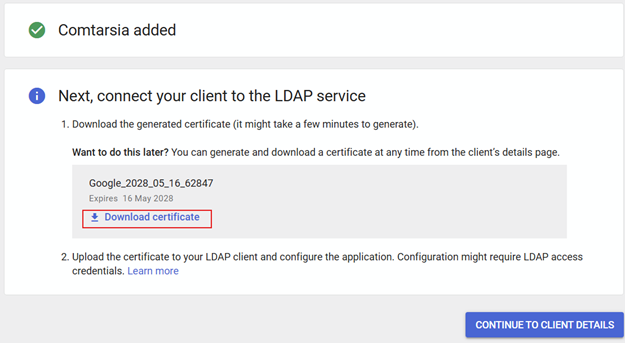
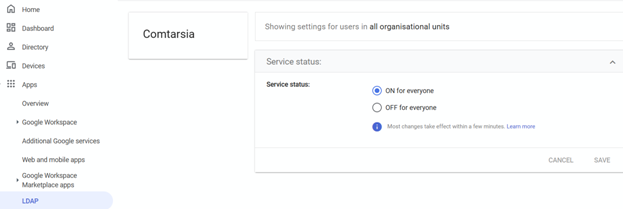
The LDAP client still needs to be enabled. Please ensure that the status for the LDAP client is set to "ON".
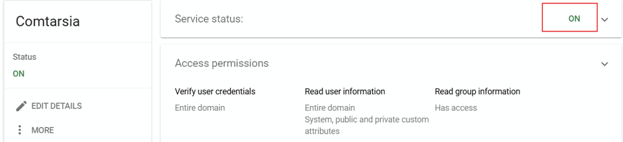
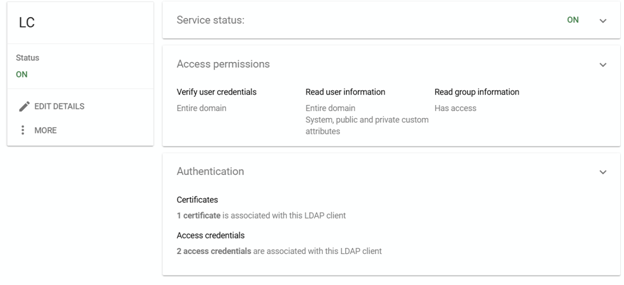
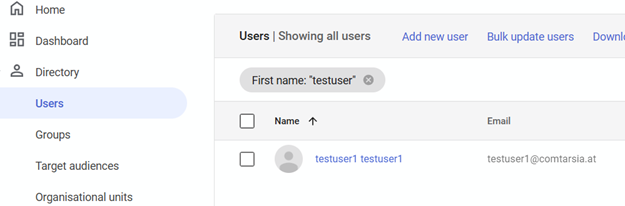
For LDAP authentication, at least one user with appropriate permissions must be created.
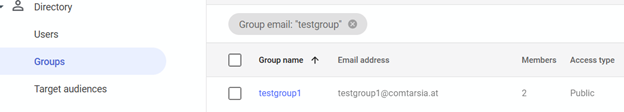
In order for local group mapping to be used in the Logon Client, at least one LDAP group must be created in which the user is a member.
3. Setup Stunnel
The tool “Stunnel” must be installed and configured. It can be installed on the same computer as the Comtarsia Logon Client or on another computer. Multiple Comtarsia Logon Clients can share one Stunnel instance.
Download the latest version from the official website: https://www.stunnel.org/downloads.html
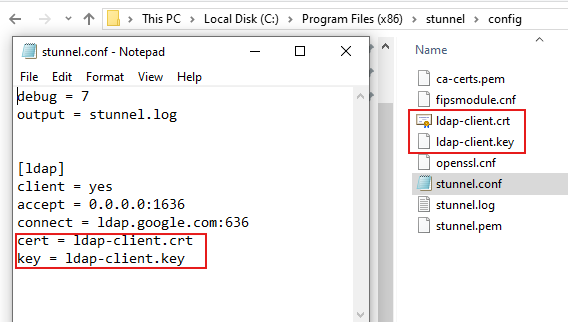
Replace the entire contents of the configuration file C:\Program Files (x86)\stunnel\config\stunnel.conf with the following parameters:
debug = 7
output = stunnel.log
[ldap]
client = yes
accept = 0.0.0.0:1636
connect = ldap.google.com:636
cert = ldap-client.crt
key = ldap-client.key
The Google client certificate files, described in the previous chapter, must now be copied to the C:\Program Files (x86)\stunnel\config\ directory and must be renamed to ldap-client.crt and ldap-client.key.
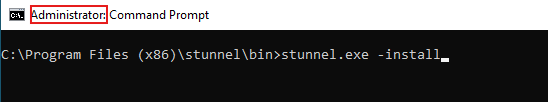
In order for the stunnel tool to start automatically in the background, it must be installed as a service. The service installation is performed via the command stunnel.exe -install by using an administrative command line window.
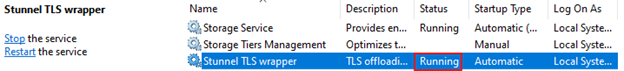
Please also make sure that the service has been installed and is running.
4. Setup Comtarsia Logon Client
For authentication on the Windows system, the Comtarsia Logon Client credential provider must be installed.
Please download the latest setup bundle from: https://signon.comtarsia.com/main/en/Download
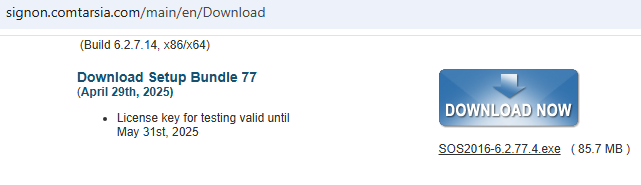
Run the installer with administrative rights and select the Logon Client module.
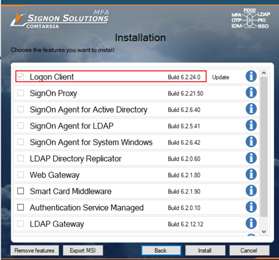
After installation, a system restart is required.
The Comtarsia Logon Client is configured by using the Comtarsia Management Console.
The authentication mode must be changed to LDAP.
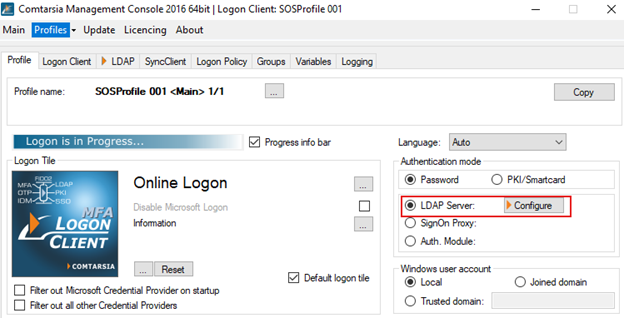
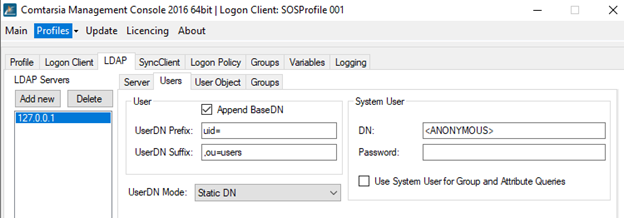
In order for the logon client to perform authentication via the stunnel interface, the LDAP host must be 127.0.0.1 (if Stunnel is installed on the same computer) and the port 1636 must be specified. The Base DN must match the Google LDAP configuration.
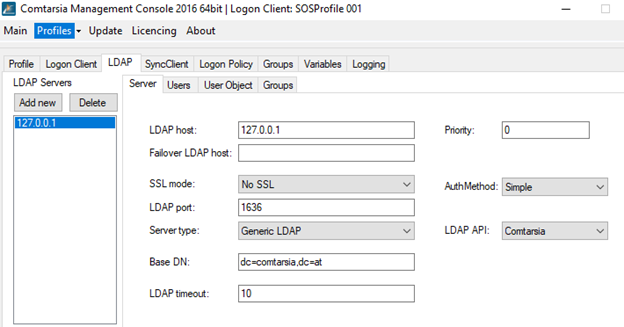
The User DN prefix must be defined as uid= and the User DN suffix must be defined as ,ou=users.
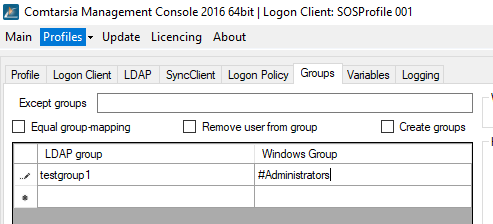
To ensure that LDAP logins work on a server system, this example shows how to assign the Google LDAP group to the local built-in group Administrators. Any LDAP group (left column) can be assigned to any local group (right column).
A system login via the Comtarsia Logon Client, by entering the short name of the LDAP user and the defined password, is now possible.

